Ransomware assaults concentrating on VMware ESXi infrastructure observe a longtime sample whatever the file-encrypting malware deployed, new findings present.
“Virtualization platforms are a core element of organizational IT infrastructure, but they usually undergo from inherent misconfigurations and vulnerabilities, making them a profitable and extremely efficient goal for menace actors to abuse,” cybersecurity agency Sygnia stated in a report shared with The Hacker Information.
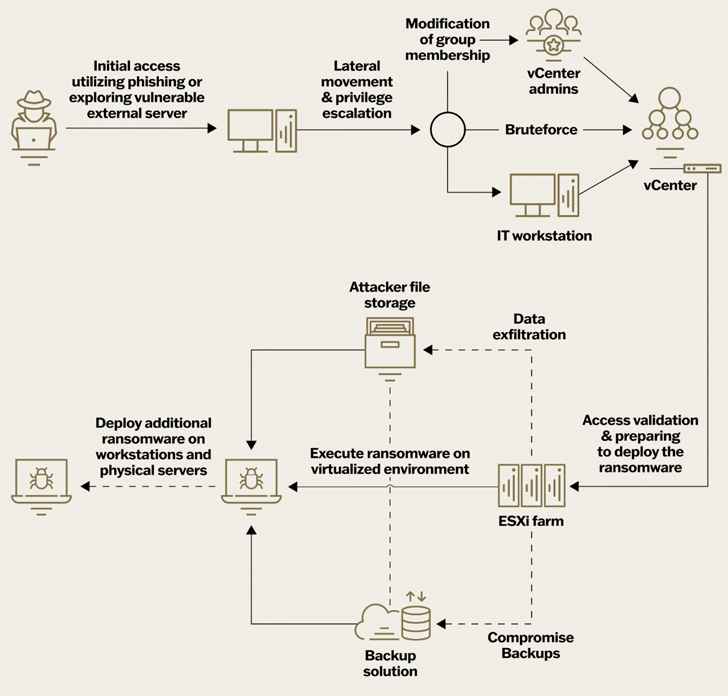
The Israeli firm, by means of its incident response efforts involving varied ransomware households like LockBit, HelloKitty, BlackMatter, RedAlert (N13V), Scattered Spider, Akira, Cactus, BlackCat and Cheerscrypt, discovered that assaults on virtualization environments adhere to the same sequence of actions.
This consists of the next steps –
- Acquiring preliminary entry by means of phishing assaults, malicious file downloads, and exploitation of identified vulnerabilities in internet-facing belongings
- Escalating their privileges to acquire credentials for ESXi hosts or vCenter utilizing brute-force assaults or different strategies
- Validating their entry to the virtualization infrastructure and deploying the ransomware
- Deleting or encrypting backup programs, or in some circumstances, altering the passwords, to complicate restoration efforts
- Exfiltrating knowledge to exterior areas equivalent to Mega.io, Dropbox, or their very own internet hosting companies
- Propagating the ransomware to non-virtualized servers and workstations to widen the scope of the assault
To mitigate the dangers posed by such threats, it is advisable for organizations to make sure ample monitoring and logging are in place, create sturdy backup mechanisms, implement sturdy authentication measures, and harden the setting, and implement community restrictions to forestall lateral motion.

The event as cybersecurity firm Rapid7 warned of an ongoing marketing campaign since early March 2024 that employs malicious advertisements on generally used serps to distribute trojanized installers for WinSCP and PuTTY through typosquatted domains and in the end set up ransomware.
These counterfeit installers act as a conduit to drop the Sliver post-exploitation toolkit, which is then used to ship extra payloads, together with a Cobalt Strike Beacon that is leveraged for ransomware deployment.
The exercise shares tactical overlaps with prior BlackCat ransomware assaults which have used malvertising as an preliminary entry vector as a part of a recurring marketing campaign that delivers the Nitrogen malware.
“The marketing campaign disproportionately impacts members of IT groups, who’re most definitely to obtain the trojanized information whereas on the lookout for professional variations,” safety researcher Tyler McGraw stated.
“Profitable execution of the malware then gives the menace actor with an elevated foothold and impedes evaluation by blurring the intentions of subsequent administrative actions.”
The disclosure additionally follows the emergence of latest ransomware households like Beast, MorLock, Synapse, and Trinity, with the MorLock group extensively going after Russian firms and encrypting information with out first exfiltrating them.
“For the restoration of entry to knowledge, the [MorLock] attackers demand a substantial ransom, the dimensions of which will be tens and a whole bunch of tens of millions of rubles,” Group-IB’s Russian offshoot F.A.C.C.T. stated.
In accordance with knowledge shared by NCC Group, world ransomware assaults in April 2024 registered a 15% decline from the earlier month, dropping from 421 to 356.
Notably, April 2024 additionally marks an finish to LockBit’s eight-month reign because the menace actor with probably the most victims, highlighting its struggles to remain afloat within the aftermath of a sweeping regulation enforcement takedown earlier this yr.

“In a shocking flip of occasions nonetheless, LockBit 3.0 was not probably the most distinguished menace group for the month and had fewer than half of the noticed assaults they did in March,” the corporate stated. “As a substitute, Play was probably the most lively menace group, adopted shortly after by Hunters.”
The turbulence within the ransomware scene has been complemented by cyber criminals promoting hidden Digital Community Computing (hVNC) and distant entry companies like Pandora and TMChecker that could possibly be utilized for knowledge exfiltration, deploying extra malware, and facilitating ransomware assaults.
“A number of preliminary entry brokers (IABs) and ransomware operators use [TMChecker] to verify out there compromised knowledge for the presence of legitimate credentials to company VPN and electronic mail accounts,” Resecurity stated.
“The concurrent rise of TMChecker is thus vital as a result of it considerably lowers the fee boundaries to entry for menace actors trying to get hold of high-impact company entry both for major exploitation or on the market to different adversaries on the secondary market.”